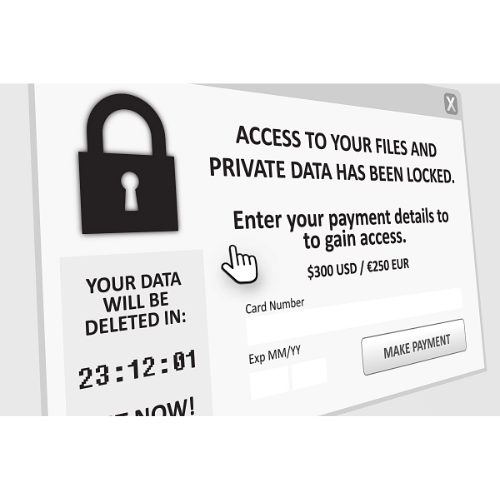
Ransomware is one of the most alarming types of cyber threats individuals and organizations face today. Derived from the words “ransom” and “software,” it is a form of malicious software or malware athat cybercriminals use to launch digital extortion schemes.
Types of Ransomware
The modus operandi of ransomware involves encryption, or locking, of a victim’s files and data, rendering them inaccessible. Upon successful encryption, the attacker then demands a ransom payment, typically in the form of cryptocurrency like Bitcoin, for the decryption key. The key, in theory, will unlock the files and return them to their original state.
Ransomware attacks can occur through various channels. Often, they originate from phishing emails or malicious websites that trick users into downloading and installing the ransomware unknowingly. Once it infiltrates a computer or network, the malware starts encrypting files.
Let’s take a closer look at the main types of ransomware, including technical details and some notorious examples:
Encrypting Ransomware
This is the most common type of ransomware. Once it infiltrates a system, it uses robust encryption algorithms (such as AES and RSA) to lock files and make them inaccessible. The victim is then presented with a ransom note demanding payment in exchange for the decryption key. It’s important to note that even if the ransom is paid, there’s no guarantee that the decryption key will be provided.
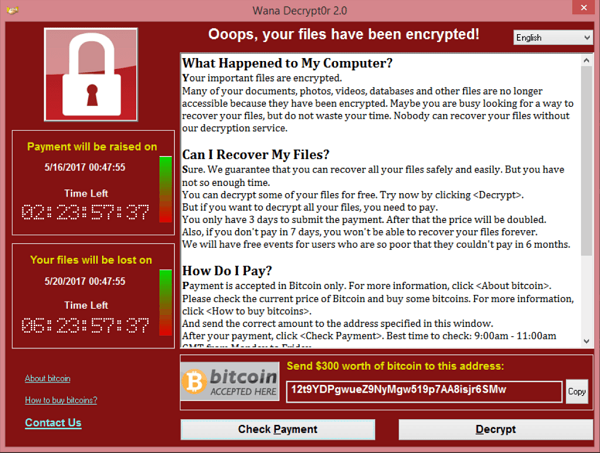
Example – WannaCry: WannaCry spread rapidly in May 2017, exploiting a Windows vulnerability known as EternalBlue. It locked files using RSA encryption and demanded payment in Bitcoin. Its spread was halted when a security researcher found a “kill switch” within the code.
Locker Ransomware
This type of ransomware doesn’t encrypt files. Instead, it locks the victim out of their device entirely, displaying a full-screen message that prevents access to the system. The user can’t access the desktop, apps, or files until the ransom is paid.
Example – WinLock: WinLock displayed pornographic images on the victim’s screen and demanded a premium SMS payment to remove them. While it didn’t encrypt files, it rendered the user’s computer unusable.
Doxware (Leakware)
Doxware threatens to publish the victim’s stolen data online unless the ransom is paid. It’s a potent form of ransomware because even if the victim has backups or can remove the ransomware, the threat of data leakage can still coerce victims into paying the ransom.
Example – Revil: Revil, active since 2019, has been associated with high-profile attacks. Along with encrypting files, it steals data and threatens to publish it if the ransom isn’t paid.
RaaS (Ransomware as a Service)
This is a business model where cybercriminals develop ransomware and sell or rent it to other criminals who then carry out attacks. The developers usually get a percentage of the profits.
Example – GandCrab: GandCrab, active from 2018 to 2019, was one of the most successful RaaS examples. It was constantly updated to evade detection and exploit new vulnerabilities.
Mobile Ransomware
As the name suggests, this type of ransomware targets mobile devices, primarily Android due to its large user base and the ability to install apps from unofficial app stores, which may not have stringent security measures.
Example – Simplocker: this was the first widespread Android ransomware. It encrypted files on the device’s SD card and demanded a ransom to decrypt them.
Crypto Ransomware
Not to be confused with Cryptolocker, a famous ransomware strain, crypto ransomware refers to a broad category of ransomware that encrypts files on the victim’s computer.
Example – Ryuk: first seen in 2018, Ryuk targets large organizations for high-ransom return. It’s typically distributed via other malware, like TrickBot or Emotet.
Understanding these types of ransomware and their typical behavior is an important part of cybersecurity, whether you’re protecting a personal device or an organization’s network. Awareness and proactive defense measures are key in preventing such attacks.
Popular Ransomware
What follows is a list of some of the most infamous ransomware strains that have made headlines around the world, causing significant disruption and financial loss.
WannaCry: this ransomware attack that occurred in May 2017 affected hundreds of thousands of computers across 150 countries. It targeted computers running Microsoft Windows, exploiting a vulnerability in the operating system to encrypt files.
Petya/NotPetya: first observed in 2016, Petya was designed to encrypt data on a computer’s hard drive. In 2017, a variant named NotPetya was used in a global cyberattack, causing major disruptions, particularly in Ukraine.
Locky: appearing in 2016, Locky spread via phishing emails containing a Word document infected with malicious macros. When activated, it encrypted a wide range of file types.
Cerber: this ransomware-as-a-service (RaaS) became prominent in 2016. It was designed not only to encrypt user files but also to read out its ransom note.
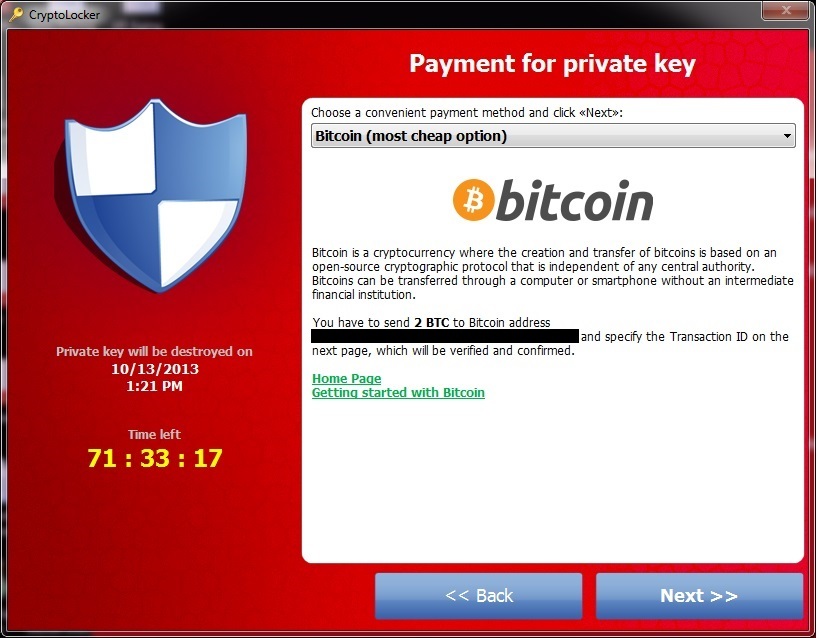
CryptoLocker: this was one of the first examples of modern ransomware and was notorious for its use of an online payment portal when it emerged in 2013. It spread through email attachments and encrypted files using RSA public key cryptography.
Ryuk: beginning in 2018, Ryuk targeted large organizations for high-ransom return. It is often distributed via other malware, like TrickBot or Emotet.
Sodinokibi/REvil: first identified in 2019, REvil is a RaaS that is commonly spread through exploits in Oracle WebLogic and is also known for its ability to disable antivirus software.
GandCrab: active from January 2018 to June 2019, GandCrab was one of the most aggressive RaaS families. It was distributed through a variety of methods, including exploit kits and phishing emails.
Dharma/CrySiS: Dharma ransomware is a variant of CrySiS and has been around since 2016. It targets Windows systems, and its encryption algorithm makes decryption nearly impossible without the private key.
Bad Rabbit: this ransomware, first seen in 2017, is suspected to be related to the Petya ransomware. It spread via a fake Adobe Flash update on compromised websites.
Preventing and dealing with Ransomware
While ransomware attacks can be devastating, there are preventive measures that individuals and organizations can take:
Back up your data: regularly backing up data to a separate system or cloud service helps ensure that, even if an attack occurs, you have another copy of your important files and data.
Update and patch your systems: keeping your software and systems updated is crucial, as updates often include patches for known vulnerabilities that ransomware can exploit.
Invest in cybersecurity: utilizing antivirus software, firewalls, and other security tools can help identify and block potential threats.
Practice safe browsing habits: avoid clicking on suspicious links, and be cautious about downloading files or software from unverified sources.
Educate and train employees: for organizations, providing regular training to employees about identifying phishing emails and practicing safe internet use can significantly reduce the risk of an attack.
In the unfortunate event that you become a victim of a ransomware attack, it’s recommended not to pay the ransom. Paying does not guarantee you’ll regain access to your files and may even encourage future attacks. Instead, report the incident to law enforcement and seek professional help from a cybersecurity firm.
Understanding the nature and risks of ransomware is key in today’s digital age. With the appropriate preventive measures, we can significantly reduce the threat and protect our data in the virtual world.